You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
Copy file name to clipboardExpand all lines: views/website/md/introduction.md
+3-3
Original file line number
Diff line number
Diff line change
@@ -90,7 +90,7 @@ The following shows a JWT that has the previous header and payload encoded, and
90
90
91
91
If you want to play with JWT and put these concepts into practice, you can use [jwt.io Debugger](https://jwt.io/#debugger-io) to decode, verify, and generate JWTs.
In authentication, when the user successfully logs in using their credentials, a JSON Web Token will be returned. Since tokens are credentials, great care must be taken to prevent security issues. In general, you should not keep tokens longer than required.
@@ -111,7 +111,7 @@ If the token is sent in the `Authorization` header, Cross-Origin Resource Sharin
111
111
112
112
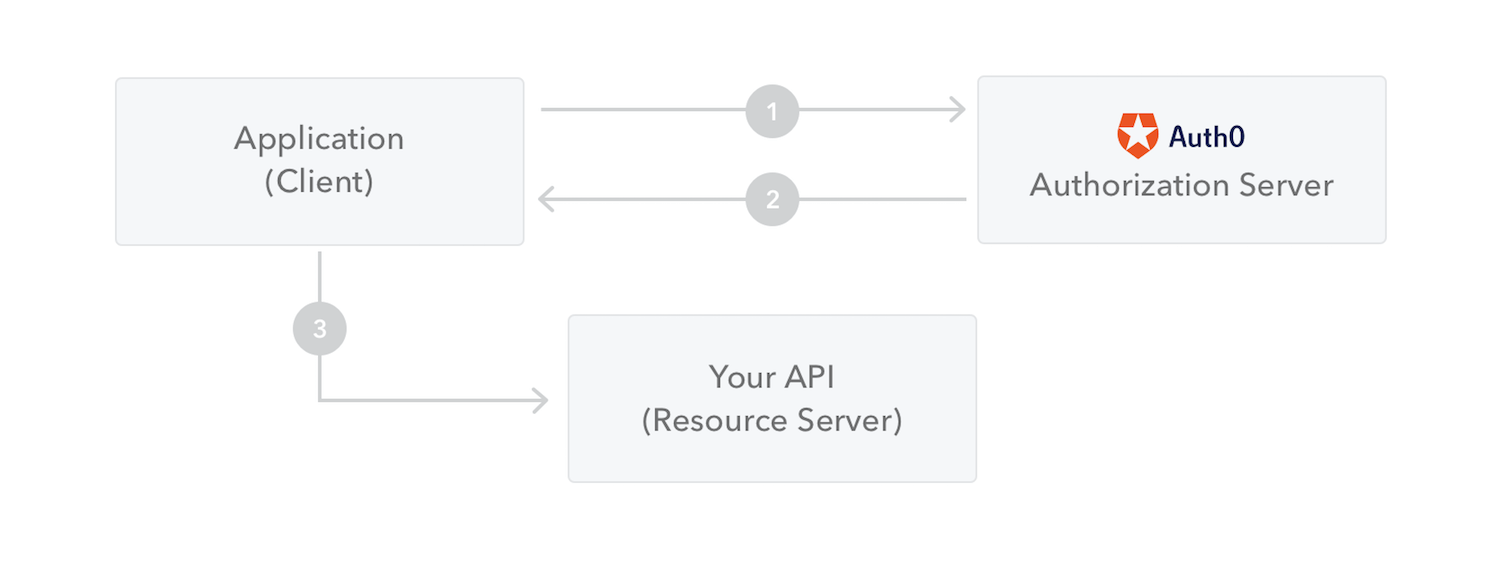
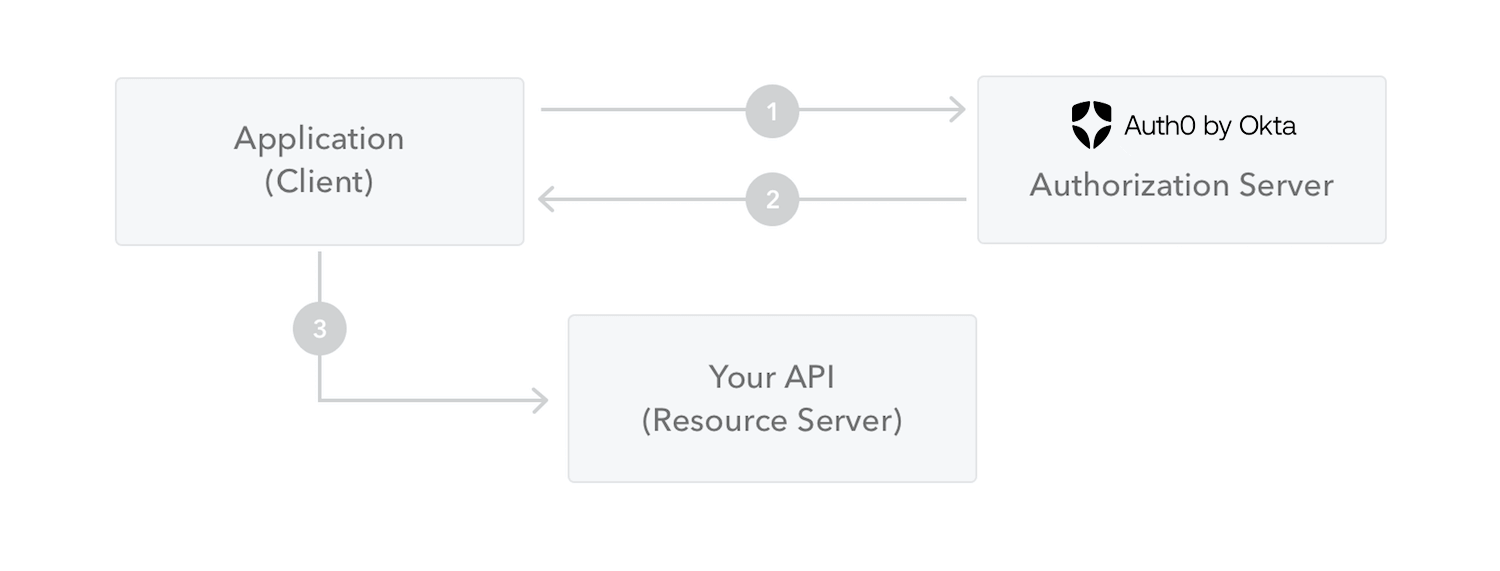
The following diagram shows how a JWT is obtained and used to access APIs or resources:
113
113
114
-
114
+
115
115
116
116
1. The application or client requests authorization to the authorization server. This is performed through one of the different authorization flows. For example, a typical [OpenID Connect](http://openid.net/connect/) compliant web application will go through the `/oauth/authorize` endpoint using the [authorization code flow](http://openid.net/specs/openid-connect-core-1_0.html#CodeFlowAuth).
117
117
2. When the authorization is granted, the authorization server returns an access token to the application.
@@ -134,4 +134,4 @@ Regarding usage, JWT is used at Internet scale. This highlights the ease of clie
134
134
135
135
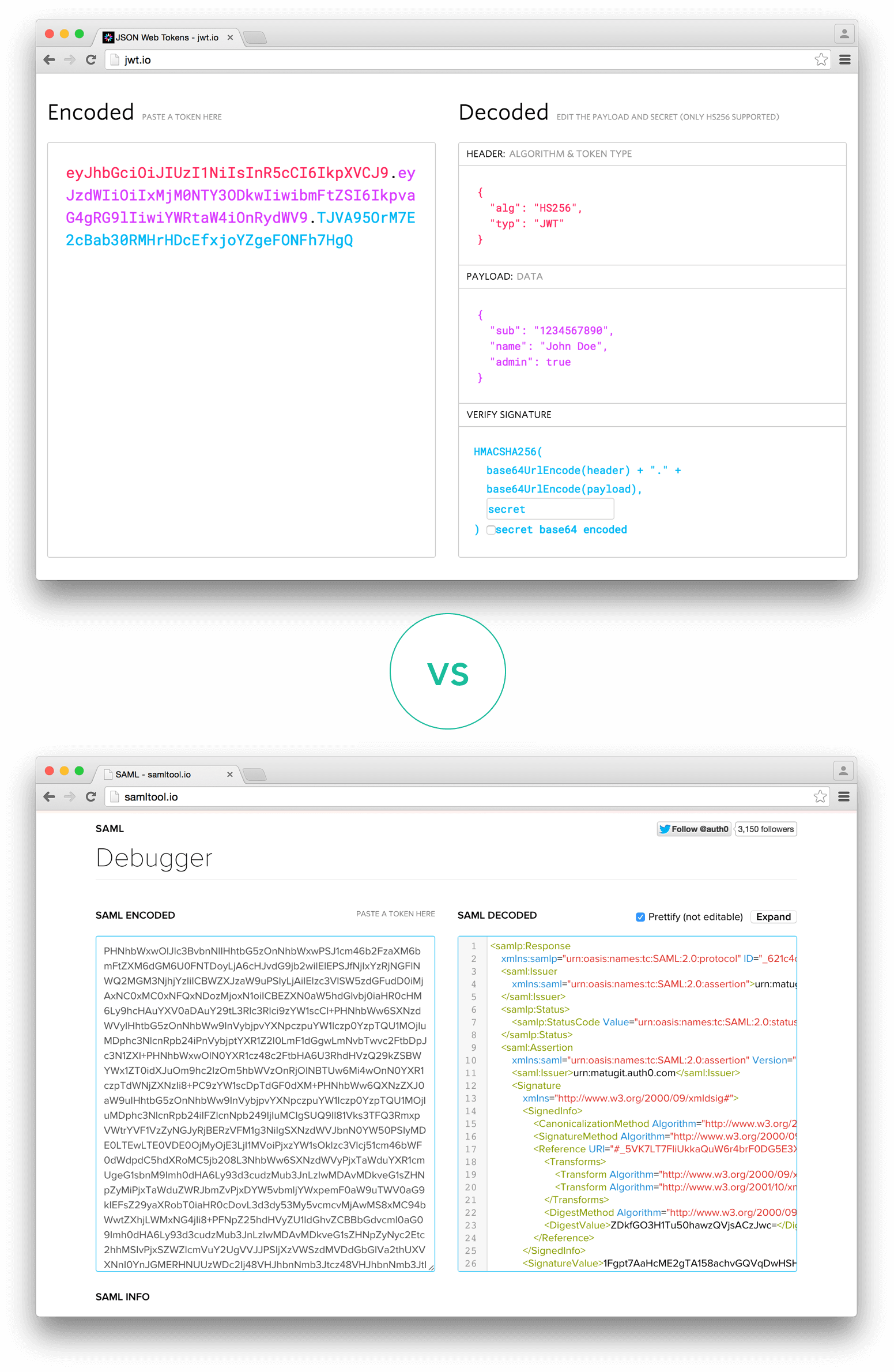
_Comparison of the length of an encoded JWT and an encoded SAML_
136
136
137
-
If you want to read more about JSON Web Tokens and even start using them to perform authentication in your own applications, browse to the [JSON Web Token landing page](http://auth0.com/learn/json-web-tokens) at Auth0.
137
+
If you want to read more about JSON Web Tokens and even start using them to perform authentication in your own applications, browse to the [JSON Web Token landing page](http://auth0.com/learn/json-web-tokens) at Auth0 by Okta.
0 commit comments